
13.01.2020
Top-Tier Russian Organized Cybercrime Group Unveils Fileless Stealthy “PowerTrick” Backdoor for High-Value Targets
The TrickBot cybercrime enterprise actively develops many of its offensive tools such as “PowerTrick” that are leveraged for stealthiness, persistence, and reconnaissance inside infected high-value targets such as financial institutions. Many of their offensive tools remain undetected for the most part as they are used for a short period of time for targeted post-exploitation purposes such as lateral movement.
Their offensive tooling such as “PowerTrick” is flexible and effective which allows the TrickBot cybercrime actors to leverage them to augment on the fly and stay stealthy as opposed to using larger more open source systems such as PowerShell Empire. The end-goal of the PowerTrick backdoor and its approach is to bypass restrictions and security controls to adapt to the new age of security controls and exploit the most protected and secure high-value networks. SentinelLabs developed mock command-and-control panels to allow the institutions to utilize them for testing detections related to “PowerTrick”.
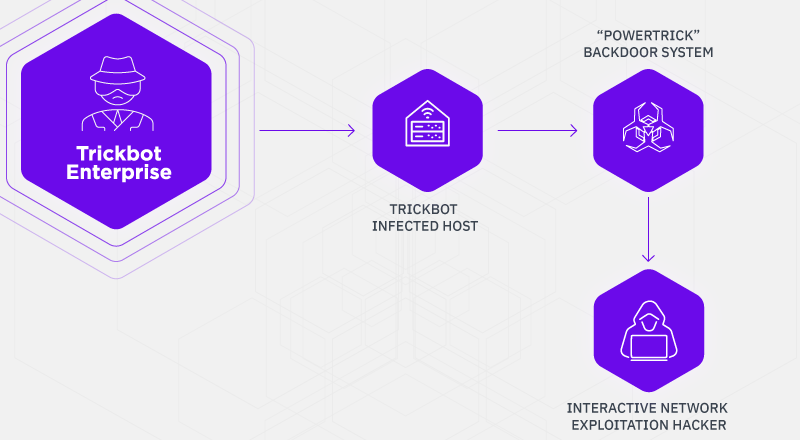
TrickBot is the successor of Dyre [1, 2] which at first was primarily focused on banking fraud in the same manner that Dyre did utilize injection systems. TrickBot has shifted focus to enterprise environments over the years to incorporate many techniques from network profiling, mass data collection, incorporation of lateral traversal exploits. This focus shift is also prevalent in their incorporation of malware and techniques in their tertiary deliveries that are targeting enterprise environments, it is similar to a company where the focus will shift depending on what generates the best revenue. This research follows SentinelLabs discovery of the TrickBot Anchor malware and its nexus to the organized groups and advanced persistent threats.
PowerTrick Discovery
SentinelLabs research into this PowerShell-based backdoor called “PowerTrick” traces back to the initial infection, we assess with high confidence at least some of the initial PowerTrick infections are being kicked off as a PowerShell task through normal TrickBot infections utilizing a repurposed backconnect module that can accept commands to execute called “NewBCtest”.
After the initial stager for the “PowerTrick backdoor” is kicked off, then the actor issues the first command which is to download a larger backdoor. This process is similar to what you see in Powershell Empire with its stager component. PowerTrick is designed to execute commands and return the results in Base64 format, the system uses a generated UUID based on computer information as a “botID.” The Victim data is then posted back to the controller. PowerTrick is simply designed to execute commands and return results
PowerTrick: Actions on Objective
Aside from the PowerTrick backdoor, the criminal actors also commonly utilize other PowerShell utilities to do various tasks. A frequent one utilized was ‘letmein.ps1’ which is a Powershell stager for open-source exploitation framework Metasploit. The letmein script, in particular, is leveraged frequently to pivot the infection to another framework. It is also used to detonate on other systems after pivoting.
The frequently used commands and actions are as follows:
- net view
- net use
- ping systems
- net use with usernames to check permissions on systems
- WMIC /node:localhost /Namespace:\\root\SecurityCenter2 Path AntiVirusProduct Get displayName /Format:List
Once the system and network have been profiled, the actors perform deletion operation and cleanup. They remove any existing files that did not execute properly and move on to a different target of choice or perform lateral movement inside the environment to high-value systems such as financial gateways. The executed tasks included a wide range of utilities such as previously shown Metasploit.
Other interesting deliveries will be discussed below:
- TrickBot Anchor Malware: TrickBot Anchor DNS variant [3] is frequently leveraged as an attack framework for enterprise environments.
- TerraLoader, “more_eggs” Backdoor: TerraLoader variant version “6.0” with more_eggs JavaScript backdoor onboard is a deployed payload, often in addition to the aforementioned Anchor DNS variant on the same systems.
- Direct Shellcode: Direct shellcode execution is a methodology for payload deployment via a hexlified parameter.
This is something we have observed frequently where the actors will modify or create new delivery systems in order to bypass restrictions and security controls.
Want to learn more about the attackers view, an analyst persective and mitigative actions? Follow the link in the references section below and download the 11 page report