
21.02.2018
17 Threat Landscape Predictions for 2018
Every day we work towards a better and safer future, but to do so, we need to understand what we can expect tomorrow. Below you will find 17 expectations from Pepijn Janssen and his Malware Intelligence Team, with a strong focuses on network threats.
1. Cryptocurrency
Cryptocurrency is used by cybercriminals to exchange or buy services and products. The fact that it is difficult to track cryptocurrency also makes it an attractive asset for cybercriminals to have. This means that the number of attacks that involve cryptocurrency miners will only increase, as it allows the cybercriminals to earn additional wealth while hijacking and controlling a device.
In addition, it also means that Cryptocurrency Exchanges will be targeted by cybercriminals, this is because of the fact that cryptocurrencies do not have the same level of security compared to banks. This same fact also means that there will be an increase in attacks performed on digital cryptocurrency wallets.
2. Browsers as Cryptocurrency Miners
Another aspect that we see an increase in is the fact that websites will hold Browser mining software that will force a users’ browser to mine cryptocurrency.
This can be initiated by the user of course, but it is also something which you need to be aware of. Mining via the browser literally means that computing power and energy will be used to craft digital value. It also means that the life expectancy of the device will drop.
3. Internet of Things
Telnet brute-force attacks and other methods are being used to hijack and control Internet of Things devices. This means that your smart home, or your wearable could become part of a huge botnet that is controlled by cybercriminals. The number of devices that are being built doubles every two years, this means it’s an interesting environment for cybercriminals and hackers to focus their malware efforts.
Forbes predicted that marketers will wake up to the IoT opportunity, and we strongly believe that the cybercrime sector will follow the same path – but with a different and more malicious focus.
In 2017, we witnessed two IoT-focused campaigns: Mirai and Brickerbot.
Mirai used IP-enabled cameras and home network gear to perform targeted DDoS attacks on Twitter, Spotify and Github. Brickerbot was used to hijack and break connected IoT devices. The Brickerbot malware author which claims to be a GreyHat hacker stated that he had broken 200000 telnet devices since November 2017.
Brickerbot carries 86 protocol and device-specific payloads which enables it to hijack and control IoT devices.
4. IoT Botnets
Mirai and Brickerbot have played a clear role in 2017 and we believe that the number of attacks performed on IoT devices will continue to increase and that IoT botnets will be used to perform DDoS attacks.
5. Mobile Malware
The increased number of mobile devices means that cybercriminals will expand their scope to include mobile devices. Mobile devices hold personal and valuable information – plus, the fact that they are being carried into virtually any environment will make it only more attractive.
6. Ransomware
The use of ransomware is expected to continue to grow as it has proved itself to be a profitable attack method for financial gain.
The use of ransomware has become easier over the past years. Ransomware builders (kits which allow you to build ransomware) have become increasingly popular and the RedSocks Malware Intelligence Team can see the evidence of this in the attacks that we have witnessed in 2017.
The diagram below shows a network overview of all the components that a ransomware sample (attack) can use.
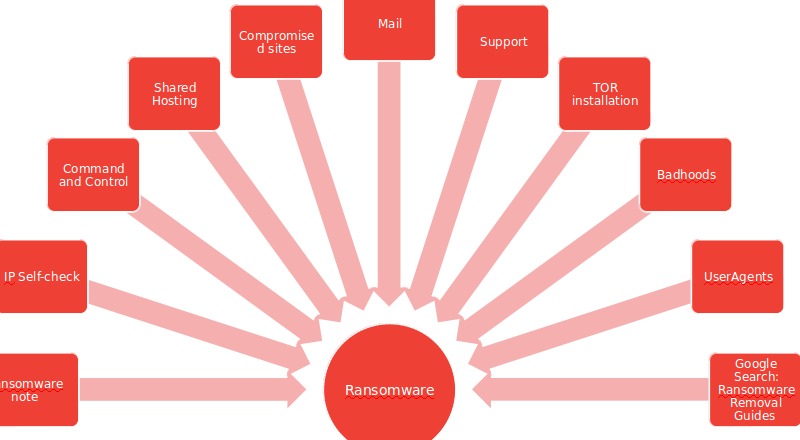
A noteworthy ransomware attack, was the BadRabbit ransomware outbreak, in that attack they used the EternalBlue SMB exploit, and believe it or not, this exploit has been crafted by the U.S. National Security Agency (NSA). The exploit was leaked by the Shadow Brokers hacker group on 14 April, 2017.
7. Ransomware + (smart) Cars
In 2017, you were able to witness a dancing Tesla car that was breached during the SHA 2017 conference in The Netherlands. A video of the dancing car has been uploaded here. We expect that in the near future attacks on smart cars, including Tesla, will continue to grow.
8. Cyber Extortion
DDoS attacks have continued to increase in frequency. In 2017, we saw various DDoS attacks that were used to extort a targeted environment. The news aggregator Feedly fell victim to a DDoS attack. In this attack, the cybercriminals demanded payment to suspend the attack on their servers. We believe that these types of attacks will continue to rise in 2018.
9. Fake Malware Removal Guides
Another interesting development during the last year is the increase in fake malware removal guides. The malware landscape is developing rapidly and new types of malware are classified on a daily basis. People with zero technical background are trying to earn a buck by providing fake malware removal guides and tools.
These tools will often worsen the situation after a successful infection by removing values that are used by the malware to operate. Various ransomware families cannot be decrypted right now, but these removal guides claim to have the way to mitigate and resolve ransomware threats while, in reality, it’s not that simple.
10. Bot News and Propaganda
Social media and news environments will play a crucial role in misinformation / propaganda. In 2017, a report was provided which clearly viewed how Russian linked actors had been buying Facebook ads to publish propaganda. Facebook was not the only platform that was being used for propaganda. Social media networks like Instagram and Twitter were also used. United States lawmakers had published a list of 65 Twitter users that are alleged to be directly linked to Russian government propaganda.
11. Attacks on Security Providers
The attacks that are performed on security vendors will continue. Security providers play a crucial role in fighting malware and malicious threats. It is for this reason that we expect that cybercriminals and other aggressive parties will continue to attempt to gather better insight into what security vendors are doing and seeing.
12. Encryption
We expect that in the near future cybercriminals will start to use cybercrime services where cypher punks will develop unique, custom ciphers for malware and software to be used in the criminal world.
The reason behind this is that cybercriminals will not trust public cryptography anymore. This also means that many in-place security solutions like SSL strippers will not be able to decrypt the encrypted traffic.
13. TLS 1.3
TLS 1.3 is a new (draft) standard internet connection encryption.
One of the main features it provides:
- Dropping support for many insecure or obsolete features including compression, renegotiation, non-AEAD ciphers, static RSA and static DH key exchange, custom DHE groups, point format negotiation, Change Cipher Spec protocol, Hello message UNIX time, and the length field AD input to AEAD ciphers.
- Prohibiting SSL or RC4 negotiation for backwards compatibility.
The second point is one of the challenges many security companies will have to solve, since this literally means that downgrading SSL will not be possible. This means that any man-in-the-middle attack will become extremely hard to implement. We expect that in the near future, each ‘secure’ browser will use TLS 1.3. Google Chrome has already been using TLS 1.3, and the library of TLS 1.3 has been included in the Go programming language which is used, maintained and developed by Google.
14. Malware Encryption
The usage of free SSL solutions in malware is increasing. Also, the installation and use of free SSL solutions has been simplified, which directly means that using and implementing encryption in (malicious) code has become more accessible. Encryption allows devices to communicate with each other without having a third party looking into your packets.
15. (Spear) Phishing attacks
Over the past few years, various databases have been breached that held millions of user login credentials. This information can be found on the web, and is being used by cybercriminals to perform (spear) phishing attacks.
16. (Cyber) Crime-as-a-Service (CaaS)
Each cybercriminal has a specific skill-set which stands out. For example, one of the cybercriminals may be experienced in building malware, another specialized in distributing the malware and as a final service, someone is providing ‘herding’ services, which in layman’s terms means that all the devices that have been infected by the malware, will be controlled and operated by the Botnet herder.
Cybercriminals, state actors and criminal organizations can use the CaaS-model to perform successful cyberattacks.
17. Advanced Persistent Threats
We expect to see new APT attacks in 2018, the (cyber) capabilities of threat actors and the preparation that is taken is continuously evolving. There is an arms race going on, and everyone is trying to stay on top. Last year we took a dive into APT 28, and published a full report on how it is possible to decrypt the APT28 X-agent rootkit traffic. X-agent is a rootkit from the APT28 malware family. The result of this research can be used to identify the victims of APT28 advances persistent threat without access to the victims or server’s workstation.